The Science Blog

The Mathematics Behind Cryptocurrency and Blockchain
In recent years, cryptocurrencies and blockchain technology have changed how we view finance, security, and transactions. These innovations are built on a strong math framework. This framework ensures they work well and stay secure. This blog post explores the math behind cryptocurrency and blockchain. It looks at how cryptography, decentralized finance, and blockchain security connect. When we grasp these math principles, we can see the cleverness and depth behind this digital revolution.
Cryptocurrencies, such as Bitcoin and Ethereum, are well-known today. However, the complex math behind them is still unclear to many. Decentralised finance (DeFi) and blockchain technology attract people because they offer security, transparency, and freedom. However, to truly grasp their potential, one must first delve into the mathematical concepts that support them.
Key Benefits / Why It Matters

The Relevance of Cryptography
Cryptography is the cornerstone of cryptocurrency and blockchain technology. It studies and uses methods for safe communication when there are enemies. In the realm of cryptocurrencies, cryptography ensures the integrity and confidentiality of transactions. Cryptography uses complex math to secure digital asset transfers. This allows transfers without needing intermediaries.
The significance of cryptography extends beyond mere security. It helps people manage their money. This way, they don’t have to depend on big banks. Decentralisation is a key aspect of blockchain technology. It enables secure and transparent peer-to-peer transactions. As a result, cryptography plays a pivotal role in fostering trust within the digital economy.
Understanding Decentralised Finance
Decentralised finance, or DeFi, represents a paradigm shift in the financial landscape. DeFi platforms use blockchain technology. This allows them to create financial tools and services without relying on traditional middlemen. This decentralisation is made possible through the mathematical principles that govern blockchain networks.
Smart contracts are central to DeFi. They are self-executing agreements. The terms are written in code. These contracts are executed on the blockchain, ensuring transparency and immutability. Smart contracts use math algorithms for automated, trustless transactions. This cuts down on fraud and human error.
Blockchain Security: A Mathematical Fortress
Blockchain security is paramount to the success and adoption of cryptocurrencies. The decentralised nature of blockchain networks brings unique security challenges. These challenges are tackled using advanced math techniques. These techniques keep the blockchain safe and unchangeable. They stop bad actors from changing transaction records.
One of the key mathematical concepts in blockchain security is the use of hash functions. A hash function is a mathematical algorithm that converts an input into a fixed-length string of characters, which is unique to each input. In the context of blockchain, hash functions are used to create unique identifiers for each block of transactions. This means if anyone tries to change the data in a block, the hash will change completely. This change will alert the network to possible tampering.
Step-by-Step Guide to the Mathematics of Blockchain
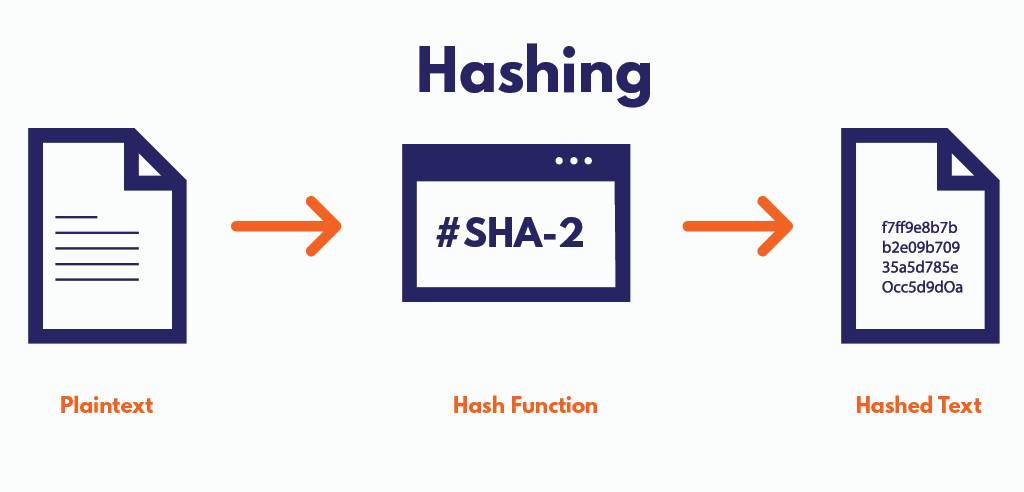
Understanding Cryptographic Hash Functions
Cryptographic hash functions are a fundamental component of blockchain technology. These functions take an input, or message, and return a fixed-length string of characters, which appears random. The key properties of cryptographic hash functions include:
- Deterministic Output: The same input will always produce the same output.
- Pre-Image Resistance: You can’t easily find the original input from its hash.
- Collision Resistance: It is highly unlikely for two different inputs to produce the same hash output.
- Avalanche Effect: A small change in the input results in a significantly different hash output.
These features keep blockchain transactions secure and intact. It’s almost impossible for bad actors to change transaction data without being caught.
The Role of Public and Private Keys
In the world of cryptocurrency, public and private keys are essential for secure transactions. These keys are generated using complex mathematical algorithms and are used to encrypt and decrypt data. The process involves:
- Key Generation: A pair of keys is generated using an algorithm such as Elliptic Curve Cryptography (ECC). The private key is kept secret, while the public key is shared with others.
- Encryption and Decryption: The public key is used to encrypt data, while the private key is used to decrypt it. This ensures that only the intended recipient can access the information.
- Digital Signatures: A digital signature is created using the private key and is used to verify the authenticity of a transaction. The signature is unique to each transaction and can be verified by anyone with the corresponding public key.
Consensus Mechanisms: Proof of Work and Proof of Stake
Consensus mechanisms are crucial for maintaining the integrity of blockchain networks. They ensure that all participants in the network agree on the validity of transactions. Two of the most common consensus mechanisms are:
- Proof of Work (PoW): In PoW, participants, known as miners, compete to solve complex mathematical puzzles. The first to solve the puzzle gets to add a new block to the blockchain and is rewarded with cryptocurrency. This process requires significant computational power and energy, making it secure but resource-intensive.
- Proof of Stake (PoS): PoS is an alternative to PoW. It requires participants to hold a certain amount of cryptocurrency to validate transactions. Validators are chosen based on the number of coins they hold and are willing to “stake” as collateral. This method saves energy and lowers the risk of centralisation. It doesn’t need a lot of computing power.
PoW and PoS both use math algorithms to secure the blockchain. This stops bad actors from taking control.
Advanced Insights / Expert Recommendations
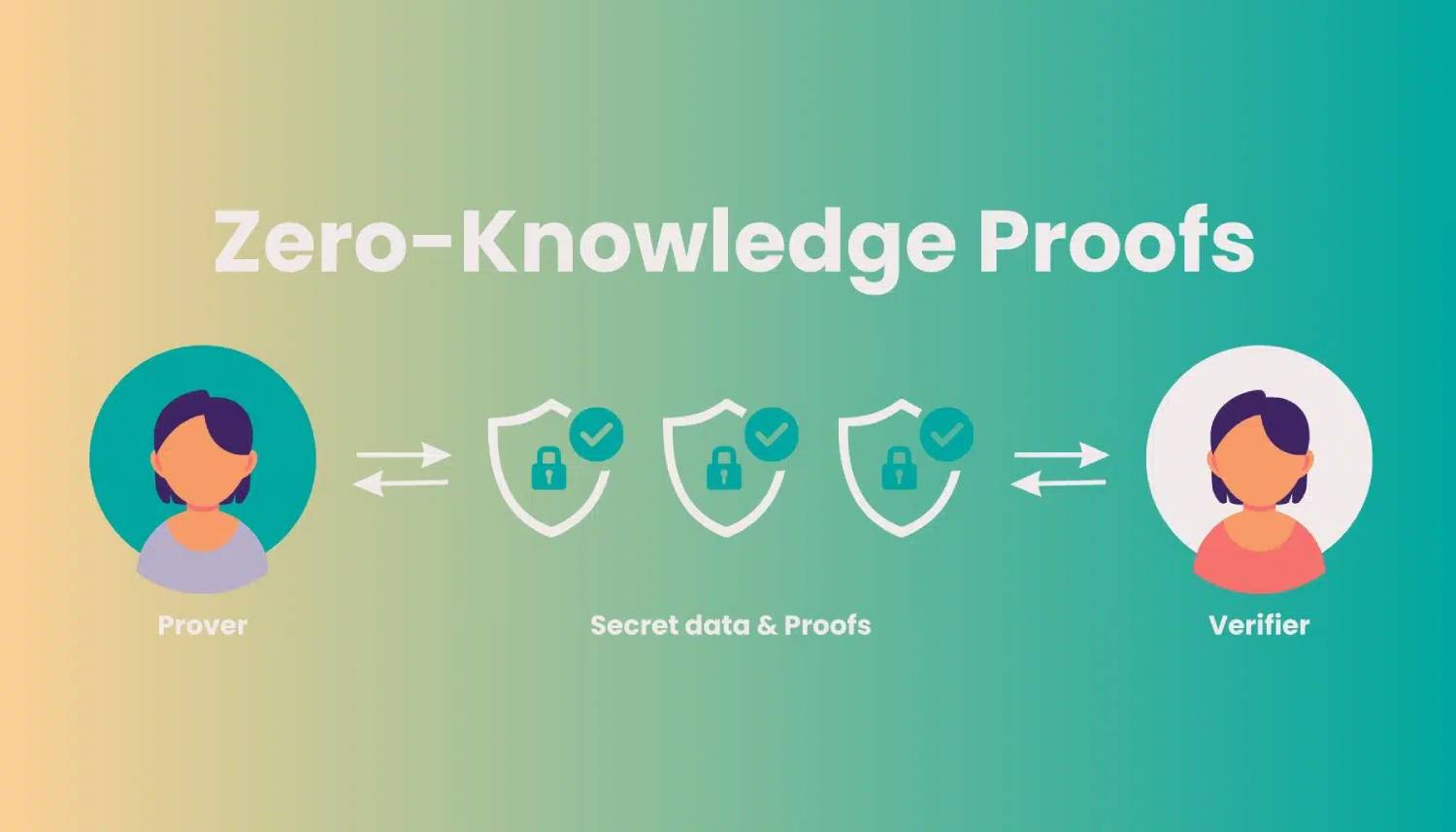
Exploring Zero-Knowledge Proofs
Zero-knowledge proofs (ZKPs) are a smart cryptographic method. They let one party show another that a statement is true. The best part? No extra information is revealed. In blockchain, ZKPs boost privacy and security. They let transactions be verified without revealing sensitive information.
ZKPs can change privacy in blockchain networks. They enable confidential transactions and better data protection. Incorporating ZKPs in blockchain protocols lets developers boost privacy. This is done without losing security or transparency.
The Future of Quantum-Resistant Cryptography
As quantum computing grows, concerns rise about its effects on current cryptographic systems. Quantum computers could break traditional cryptographic methods. This poses a big risk to blockchain security.
To address this challenge, researchers are developing quantum-resistant cryptographic algorithms. These algorithms can resist attacks from quantum computers. This keeps blockchain networks secure. As quantum computing grows, creating and using quantum-resistant cryptography will matter more and more.
The Mathematical Backbone of Blockchain & Cryptocurrency
The mathematics behind cryptocurrency and blockchain technology is both intricate and fascinating. When we understand the cryptographic principles behind these innovations, we see their security, transparency, and autonomy. The digital economy is changing fast. As it grows, math will play a bigger role in finance and technology.
If you’re curious about cryptocurrency and blockchain, look into the math behind them. Understanding cryptography, decentralised finance, and blockchain security opens new opportunities. This field is changing quickly, so it’s important to stay informed.









